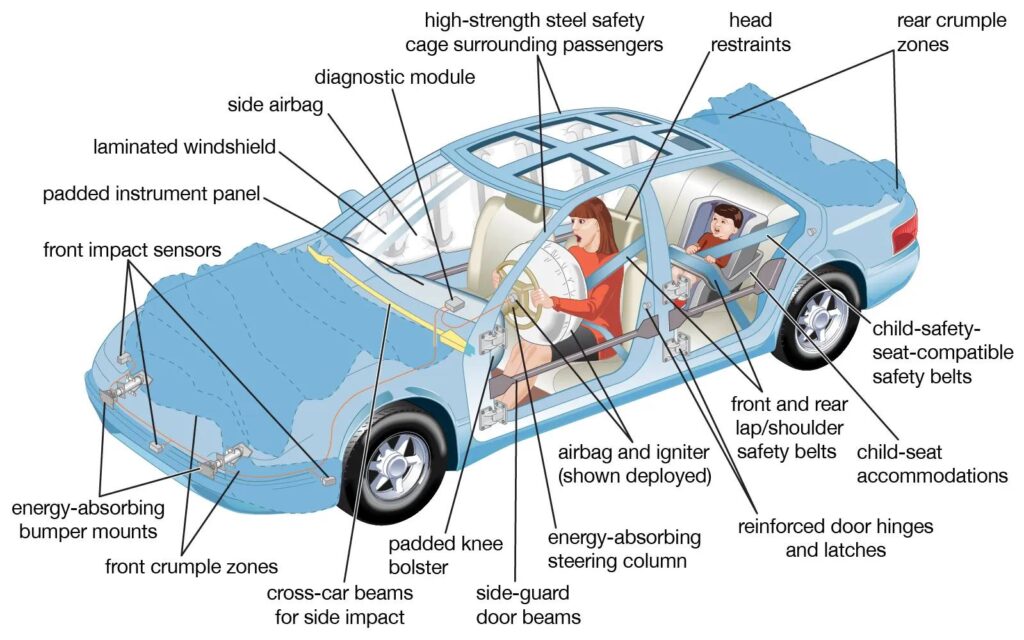
Why do I need to maintain a firewall subscription?
You might think it strange to start an article about firewall subscriptions by first talking about cars, but I promise this is perfectly relevant! If

You might think it strange to start an article about firewall subscriptions by first talking about cars, but I promise this is perfectly relevant! If

Today Fortinet announced a critical authentication bypass in its FortiGate products that could lead to administrator access. This vulnerability, CVE-2022-40684, has been patched and admins
For as long as we can remember, having antivirus (AV) software installed and updated was an important aspect of a healthy cyber security posture. However

91% of cyber attacks begin with a phishing email. Phishing remains the most common and successful way for hackers to get their foot in the

Phishing is a cybersecurity attack where the perpetrator pretends to be a trusted source through an email. The thief may masquerade as your bank or

On Friday, a vulnerability called “Log4j” that effects a large variety of consumer and business applications was revealed. This threat effects a tool that many
Changing Landscape of Cyber Security Cyber Security has always been a moving target. In the past, bad actors would hunt and search for their targets.
Kaseya VSA Hack On Friday, a popular IT tool called Kaseya VSA was hacked. The exploit was a “zero day” vulnerability, which means it was

Yesterday a critical vulnerability with Windows operating systems was revealed. The exploit, called PrintNightmare, takes advantage of a weakness with the Windows Print Spooler service.
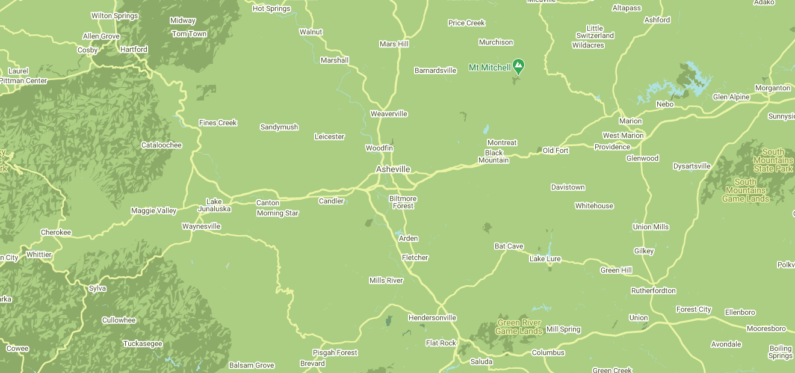
Vulnerable Exchange Servers In the wake of the Exchange Zero-day vulnerabilities, Advanced Data was concerned about how many vulnerable servers were left in our region.
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
We Schedule a call at your convenience
We perform a discovery of your current and future needs
We prepare a proposal