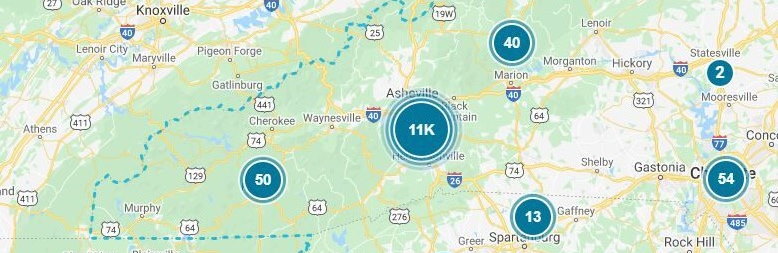
Recent regional and cloud outages
Within the past several weeks we’ve witnessed an unusually high number of outages that have impacted our clients in WNC. Some have been weather related

Within the past several weeks we’ve witnessed an unusually high number of outages that have impacted our clients in WNC. Some have been weather related
In my first post on showing the client IP addresses through a Barracuda ADC load balancer, I showed how to get Direct Server Return to work for
In order to see the client origination IP address on the real back-end servers when a Barracuda ADC load balancer is used there are two
Tips on tuning VMware ESXi for EqualLogic SANs. Install Dell MEM Download from here: https://eqlsupport.dell.com/support/download.aspx?id=1484 Important: Unzip the package and inside the package is another zip
To get the best performance out of VMware’s iSCSI initiator it’s a good idea to enable jumbo frames on the ESX hosts. First configure a new vSwitch dedicated to
With Windows 7 public availability around the corner, ADNS will be making the move this Friday. We will report our experiences on this blog
It never hurts to have a quick reference for Linux administration commands, so I wanted to put out some helpful items for user, file, directory,
As Windows Server 2008 takes it’s place in more data centers, serving as a domain controller, design changes are starting to impact end users. One
After installing WSS3 SP2 on a clean install of Server 2008 x86 SP2 STD, and using SQL 2008 SP1 as the backend, I could not get any search results. The setup is about as simple of a farm installation you can get, it is for a small number of users, and demonstration purposes, so everything is installed on a single machine virtualized on an HP server running VMware ESXi 3.5. There are two site collections using different application pools, one enabled for anonymous access, and the other not.
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
We Schedule a call at your convenience
We perform a discovery of your current and future needs
We prepare a proposal