
Thoughts on the Cisco ENCOR 350-401 Exam
Recently I passed the Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam. Wow what a mouthful! With the current generation of Cisco certs,

Recently I passed the Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam. Wow what a mouthful! With the current generation of Cisco certs,
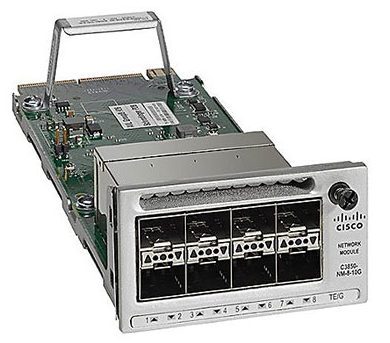
We ran into an issue where a Cisco 3850 switch (3850-12X48U) lost the ability to use the its C3850-NM-8-10G network module after a firmware upgrade.

Packet Capture on a Remote Cisco Device Typically when I need to do a packet capture on a remote Cisco IOS/IOS-XE device, I use RSPAN

This post is part three to Why We Love Continuing Education and Certifications and How I Study for IT Certification Exams There’s a genre of

This post is part 1 in a three part series which includes How I Study for IT Certification Exams and What Certs Should My IT Team
We changed a customer from PRI to SIP trunk and after the change, the Exchange UM stopped working for calls coming in from the outside.
On the pre 4000 series ISRs you would use the regular Cisco escape sequence to exit a service module — CTRL-SHIFT-6 followed by X. In
The Cisco ASA firewall can run as virtual host for multiple virtual ASA’s known as contexts. We recently ran into an issue where a memory leak made
Had an issue where I was not able to successfully upgrade the IOS firmware on a Cisco 4351 router. This model of router runs IOS-XE
The Cisco 3750x switch does not support NetFlow natively, but the C3KX-SM-10G module has ASICs that support NetFlow. With the C3KX-SM-10G module, NetFlow can only
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
We Schedule a call at your convenience
We perform a discovery of your current and future needs
We prepare a proposal